Of Corporate Data Is Now Stored On The Cloud
search engine that enables customers to look for illegal merchandise from many Darknet Markets at once. As a outcome, illicit data shall be much easier to search out for any cybercriminal. Some of the favored darknet browsers are Freenet, Tor, GNUnet, I2P, OneSwarm, RetroShare, and so forth. A different network that is encrypted and is created upon the existing internet is Darknet. It can solely be accessed through the use of some specific configuration of the tools and software program.
In one such dialogue, an actor claimed that Winzen was compromised whereas accessing baby abuse content material. Tor, also called The Onion Router, is an instance of Darknet. A Tor browser is required to enter Tor’s community, and whereas on a regular basis web web sites may be accessed utilizing Tor, there are hidden services and websites that can not be accessed on an strange web browser. Built on prime of the existing web, it’s an encrypted community that wants tools or software program to access. Conventional protocols used on the internet, however, may not work when utilizing Darknet.
When folks consider the darkish internet, a number of prominent examples come to thoughts. Dark net web sites that attract media consideration are normally getting used for illegal functions.
The name indicates that our browsing does not go deeper than the surface of the web. There is definitely criminality on the darknet, as there is on the open web. Portraying the darknet as primarily, or even solely, for criminals ignores the societal forces that push individuals towards these anonymous networks.
- For instance, educational databases are only obtainable to college and students, and corporate networks are solely available to employees.
- Peer-to-peer networks and self-hosted websites are additionally part of the darknet.
- Sites right here are not listed by search engines like google and yahoo because they’re simply not accessible to them.
Encryption And The Dark Net
Tor is a volunteer-run service that provides each privateness and anonymity on-line by masking who you’re and where you’re connecting. The service additionally protects you from the Tor community сайт гидры hydra ссылка itself—you possibly can have good assurance that you just’ll remain nameless to other Tor customers.
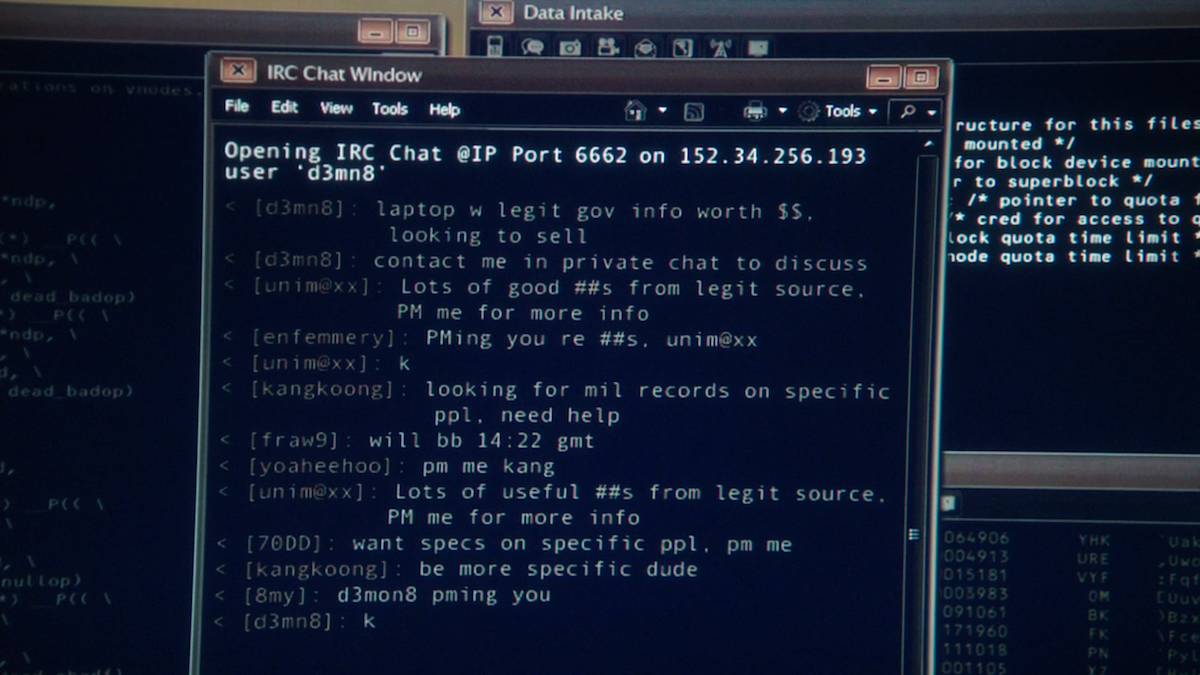
So, whenever you look for opinions about DNM, particular DNM distributors, new fraud strategies or you just don’t know the place to buy one thing, that forum is a first-place many Darknet users go. It additionally applies to those that chase after tutorials on tips on how to fraud, new providers in DNM, final events in Darknet or anything linked to Darknet, frauds, medication or another illicit exercise. On this discussion board, there are many sections, which are clearly about an criminality like Fraud, Carding, Fraud Resources, Counterfeiting, Dark Markets, Fake ID, Fake Money, LSD, Drug Manufacture, Malware, Hacking, and so on.
Tor browser is an efficient tool, but it doesn’t supply the same degree of safety and security that a VPN does. You can use Tor browser and a VPN collectively to mix their powers and maximize your privacy. Even should you’re solely using Tor browserto legally browse the web, the truth that you’re linked to Tor can potentially flip you into a goal for presidency surveillance. US authorities companies just like the NSA and FBI are very invested in looking for ways to track Tor customers’ exercise.


